Aleo and the Architecture of Trustless Privacy: How Zero-Knowledge Proofs Power the First Private Smart-Contract Blockchain
Executive Summary
This article includes three summaries written for different types of readers:
🟦 For the Curious: New to crypto or just exploring? Start here.
🟨 For the Enthusiast: Know your staking from your slashing? This is for you.
🟥 For the Builder / Founder: Deep dive into system design, trade-offs, and strategic context.
Choose the one that best matches your background or read them all for a layered understanding.
🟦 For the Curious (Beginner)
Blockchains made digital trust possible.
For the first time, strangers could coordinate value and logic without intermediaries, because everything was transparent. But that same transparency soon became a flaw.
Every wallet, payment, and smart-contract call exposed user data to the entire world.
The Web3 that promised autonomy instead created the most visible financial system ever built.
Aleo flips that model.
Unlike other blockchains, Aleo’s ledger doesn’t store public balances or state variables, all user data is encrypted by default. Yet the network still verifies every transaction and keeps everyone honest.
It works because, instead of showing the world your data, Aleo proves mathematically that your transaction followed the rules.
It uses zero-knowledge proofs, a type of cryptography that lets anyone verify a statement is true without seeing the underlying information.
A user (or a delegated prover) runs a program privately on their own machine and generates a small cryptographic proof. They send that proof, not their data, to the blockchain.
Validators check the math in milliseconds and update the ledger with new encrypted commitments and an updated state root.
They can see that a valid transaction occurred, but nothing about its private contents.
The result is a blockchain that remains transparent and trustless, yet no one has to expose their information to use it.
Aleo keeps the core promise of decentralization, verifiable integrity, while restoring something the digital world lost along the way: privacy by default.
🟨 For the Enthusiast (Intermediate)
Aleo’s core innovation is separating execution from verification. On most blockchains, every node re-executes every transaction to confirm the state is correct.
Aleo flips this model: users run the computation off-chain, and submit a zero-knowledge proof showing it was executed correctly. The blockchain verifies the proof instead of re-running the work, making the system faster, more efficient, and private by default.
Developers write applications in Leo, a high-level, domain specific language built for zero-knowledge circuits. When run, Leo code executes inside snarkVM, which generates a zk-SNARK, a concise mathematical receipt proving the computation followed the rules.
Validators running snarkOS verify this proof using the program’s public verification key; they never see private inputs, outputs, or identities.
All private state on Aleo is stored as encrypted records, similar in spirit to Bitcoin’s UTXOs, individually owned, consumed, and replaced.
But unlike UTXOs, Aleo’s records are fully encrypted: only the owner can decrypt them.
The blockchain sees only opaque commitments to these records and updates a new Merkle-tree root that represents the encrypted global state.
Consensus is handled by AleoBFT, a fast proof-of-stake protocol inspired by Narwhal and Bullshark. In parallel, Proof-of-Succinct-Work (PoSW) incentivizes independent provers to generate zk-proofs efficiently. This creates a real market for zero-knowledge computation, pushing hardware optimization, circuit efficiency, and scaling the network’s proving capacity over time.
Together, PoS and PoSW form a hybrid system that rewards both staked capital and computational contribution. The result is a blockchain that is light to verify, private by design, and horizontally scalable.
Instead of a global computer that re-runs everything, Aleo becomes a global verifier, a network that trusts only mathematics, not visibility.
🟥 For the Builder / Founder (Advanced)
Aleo is the first full-stack zero-knowledge Layer 1 designed for private programmability.
It doesn’t just bolt ZK proofs onto an existing blockchain model, it rebuilds the entire stack around them.
Leo defines the application logic, snarkVM executes that logic off-chain, and snarkOS + AleoBFT verify proofs and maintain encrypted global state.
Together, they form a cohesive execution environment where privacy is the default and transparency is something developers opt into, not out of.
A key design element is Aleo’s dual state model: programs can define both private state (encrypted records) and public state (plaintext variables).
Developers explicitly choose what should be visible and what should stay confidential.
This enables selective disclosure: users can reveal a specific field, share a view key with an auditor, or prove they met a condition without exposing underlying data.
It’s privacy with tunable transparency, something traditional blockchains cannot express.
Off-chain execution and on-chain verification introduce a new paradigm:
you don’t publish data or computation results to the blockchain, you publish proofs that the computation was correct.
This unlocks design space for applications that were previously impossible:
private DeFi with hidden positions, identity systems with zero-knowledge attestations, auditable-but-confidential enterprise workflows, and compliance tools where rules are verifiable but sensitive data never leaves the user.
Economically, Aleo aligns incentives across two domains.
Validators secure consensus and verify proofs through Proof-of-Stake.
Independent provers supply the computation needed for zk-SNARK generation through Proof-of-Succinct-Work, creating a competitive market for zero-knowledge computation.
This dual-market structure balances capital and hardware, and may become a template for future decentralized compute networks.
The trade-offs are real, proving is resource-intensive, hardware may concentrate, and privacy regulation remains unsettled.
But strategically, Aleo’s value is clear: it turns zero-knowledge from an optional feature into a programmable execution model.
Where earlier chains proved that code can move money or logic, Aleo aims to prove that code can stay private and still be trusted.
Acknowledgments
This article benefited from technical review and feedback from @zklim5389 and @snarkworld from the Aleo Team.
Their input helped refine explanations of encrypted state, delegated proving boundaries, and Aleo’s proving and consensus architecture. Any remaining errors are our own.
Introduction – From Transparency to Trustless Privacy
When Bitcoin was born, openness was the revolution.
Every transaction was visible, every rule was public, every node could verify everything.
Transparency became the foundation of trust – no secrets, no intermediaries, just math.
Then we built thousands of blockchains on that same idea,
and slowly realized we’d created systems where nothing is ever private again.
Every wallet reveals its history.
Every smart contract leaks what users are doing.
Even pseudonymous addresses can be traced through patterns and timing.
Transparency is perfect for auditing a protocol. It’s terrible for being a person.
You can’t run a business, pay employees, or even trade without leaving a permanent trail for competitors, bots, or anyone who cares to look. In a world built on blockchains, privacy became the new scarcity. And that led to a question that haunted developers for years:
How can a network stay trustworthy if nobody can keep a secret?
To reach consensus, every node must agree on the same state.
Traditionally that meant re-executing the same code and seeing the same data.
But the moment you hide information, nodes can’t check the result.
If they can’t check, they can’t trust.
If they can trust, privacy is gone.
This was the deadlock, the privacy paradox of blockchains. Until a new class of cryptography offered a way out.
The Zero-Knowledge Breakthrough
Imagine you have two balls, one red, one green, that look identical.
Your friend is color-blind and doesn’t believe they’re different.
You want to prove they are, without revealing which is which.
So you play a simple game:
-
Your friend hides both balls behind their back and may swap them.
-
They show them again and ask, “Did I switch them?”
-
You answer correctly every time.
After many rounds, your friend is convinced you really can tell,
even though they never learned which ball is red or green.
That’s a zero-knowledge proof in human form:
you prove you know something true, without revealing the secret itself.
In cryptography, the “balls” are private data, and the “game” is a mathematical challenge.
The prover keeps the secret (inputs or identity) but responds in a way that convinces the verifier that the rules were followed.
Modern zero-knowledge proofs compress this whole back-and-forth into a single, tiny piece of math that anyone can verify instantly.
How Aleo Turns It Into a System
Aleo starts from a simple but radical idea: the entire blockchain should be encrypted.
Balances, application state, and user interactions all live as encrypted records, hidden from everyone except their owners. On a transparent blockchain this would normally break consensus, if nodes can’t see the data, they can’t agree on whether a transaction is valid.
Aleo solves this with zero-knowledge proofs.
Users don’t reveal their data, instead, they reveal a proof that their private computation followed the program’s rules.
In practice, the proof asserts a simple statement:
“I executed this code correctly and followed the rules.”
This lets nodes verify correctness without seeing any of the underlying data.
Building on this foundation, Aleo changes how blockchains execute programs.
Instead of every node re-running every transaction like Ethereum, users (or delegated provers) run the program off-chain and generate a zk-SNARK proving it was executed correctly.
The blockchain never sees the inputs or outputs.
It only stores encrypted commitments and a new state root, a mathematical fingerprint showing the encrypted global state has changed without revealing how.
Validators verify the proof in milliseconds using the program’s public verification key.
They can confirm the rules were followed even though none of them can see the underlying data.
In Aleo, computation happens privately, verification happens publicly.
This architecture makes private balances, private transactions, and private application logic not only possible, but native.
Privacy and verifiability stop being a trade-off, Aleo unifies them in the same design.
Aleo’s Place in the History of Private Blockchains
Zero-knowledge proofs aren’t new. Before Aleo, several projects used them, but only for specific use-cases like private payments or blockchain compression. Aleo is the first to turn that math into a full, private computing platform.
| Project | Launch / Status | What It Enabled | Why It Differs from Aleo |
|---|---|---|---|
| Zcash (2016) | Mainnet | Private transfers using zk-SNARKs | Fixed transaction logic – no smart contracts |
| MimbleWimble / Grin / Beam | 2018–2019 | Confidential transactions | Not programmable |
| Secret / Oasis Network | 2020 | Encrypted smart-contract execution | Relies on trusted hardware (SGX), not ZK cryptography |
| Aztec 2.0 (Ethereum L2) | 2021–2022 | Private payments and limited logic on Ethereum | Layer-2 rollup; inherits Ethereum’s public base layer |
| Mina | 2021 | Recursive SNARKs to compress chain size | Transparent by default; not private execution |
| Aleo | Testnet 2021 → Mainnet 2024 | Private-by-default smart contracts and encrypted state | First L1 built entirely around off-chain execution + zk-proof verification |
Unlike its predecessors, Aleo doesn’t add privacy to an existing chain, it’s built around it. Every program runs privately by default, written in Leo, executed inside snarkVM, and verified through zk-SNARK proofs by snarkOS validators.
This vertical integration, language, virtual machine, and consensus, makes Aleo the first fully private, general-purpose blockchain, where privacy isn’t an optional layer but the architecture itself.
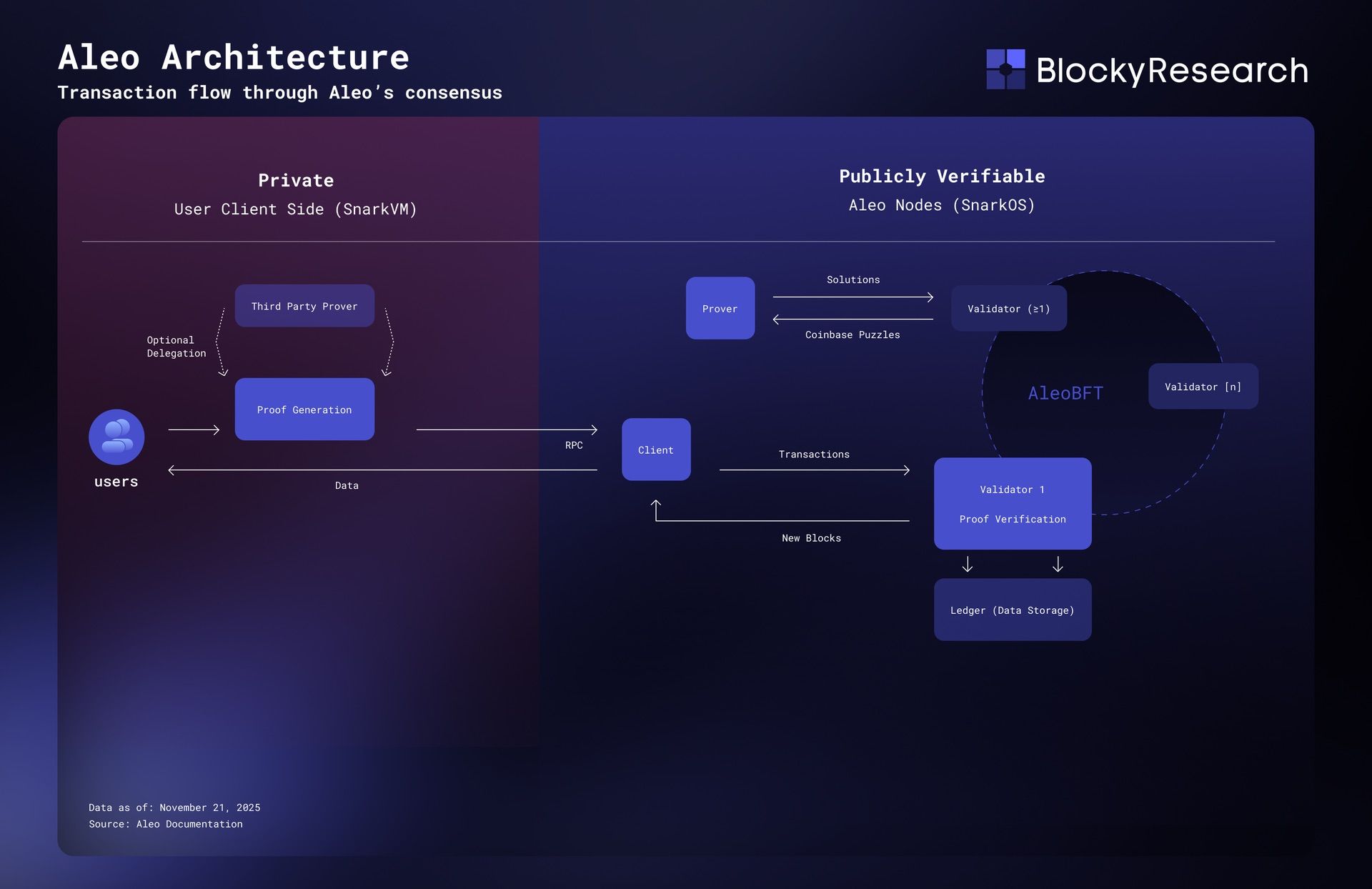
How Aleo Works
Aleo’s architecture is built around a simple idea:
users compute privately, the blockchain verifies publicly.
Every program, transaction, and state update follows this pattern.
To understand how, we’ll look at Aleo’s three core components – snarkVM, snarkOS, and Leo – and trace what happens when you execute a private transaction.
The Core Mechanism: Compute Locally → Prove Globally
Traditional blockchains require every node to re-execute every line of code to stay in sync.
Aleo flips that model.
-
Users run programs locally on their own device (or a delegated prover).
-
The local execution produces a zero-knowledge proof that the computation followed the program’s rules.
-
The proof, plus encrypted outputs, is sent to the network.
-
Validators verify the proof in milliseconds instead of re-running the code.
-
If it checks out, the blockchain updates its encrypted global state – a Merkle-tree root that commits to all private records.
The result: the network stays consistent, but no one ever sees your data.
The Building Blocks
snarkVM – The Private Virtual Machine

The Aleo Virtual Machine executes programs off-chain and produces proofs instead of plaintext results.
It translates Leo code into arithmetic circuits (R1CS) and uses zk-SNARKs to prove that all constraints were satisfied. SnarkVM handles the heavy work – field arithmetic, circuit synthesis, and proof generation – all done privately on the user’s machine.
snarkOS – The Blockchain Layer
snarkOS is the node software that maintains the public ledger and consensus.
Its job isn’t to recompute programs, but to:
-
verify proofs produced by users,
-
store encrypted commitments (records), and
-
update the global Merkle root that represents the encrypted state.
Consensus runs on AleoBFT, a proof-of-stake protocol inspired by Narwhal & Bullshark.
Validators agree on block order and state roots with instant finality, while separate “prover” nodes compete to generate proofs for rewards under Aleo’s hybrid Proof-of-Succinct-Work model.
Leo – The Language of Private Apps
To make zero-knowledge programming accessible, Aleo provides Leo, a domain specific language language purpose-built for private smart contracts.
Developers explicitly mark which data is public or private, and the Leo compiler automatically transforms the program into the underlying SNARK circuits.
The key advantage is that Leo lets developers build complex, non-trivial zero-knowledge circuits from scratch without any cryptography experience.
All the hard parts, constraint generation, witnesses, proving keys, circuit wiring, are handled by the compiler and snarkVM.
The result is a language that hides the math while preserving performance, enabling developers to build private DEXs, encrypted games, identity systems, or compliance-safe enterprise logic without touching low-level cryptographic code.
The Life of a Private Transaction
Let’s trace a typical example: Alice sends 30 Aleo credits to Bob.
-
Local execution.
Alice’s wallet runs the transfer_private() function of the credits.aleo program inside snarkVM. It consumes one of her existing private credit records (an encrypted balance) and a separate fee record.The program then produces:-
a 30-credit record encrypted to Bob’s address,
-
a 20-credit change record encrypted back to Alice,
-
and burns the fee record, paying the network fee.
The fee is handled as a dedicated transition within the same transaction, so the wallet must select a fee record just like any other record input.
-
-
Proof generation.
snarkVM produces a zk-SNARK proof that:-
the total outputs equal the input,
-
Alice was authorized to spend the record, and
-
the program logic of
credits.aleowas followed.No amounts, keys, or addresses are revealed.
-
-
Transction submission.
The wallet sends the proof and the encrypted outputs to a snarkOS node.
Validators verify the proof using the stored verification key forcredits.aleo. -
Ledger update.
Once verified, validators append the transaction to a block.
The old record’s nullifier is revealed and marked as spent, the new record commitments are inserted into the Merkle tree, and the global state root updates to reflect the change. -
Record scanning.
Bob’s wallet scans new commitments, tests which ones decrypt with his view key, and discovers the 30-credit record. To everyone else, it’s just an opaque ciphertext – only Bob can read it.
From start to finish, the network never learns who sent what to whom – yet every node can mathematically verify that the transaction is valid.
Why This Matters
This execution model gives Aleo several advantages:
-
Scalability: Verifying a proof is constant-time, regardless of how complex the original computation was.
-
Privacy by default: All data and state are encrypted; only proofs and commitments are public.
-
Parallelism: Transactions touching different records can be verified simultaneously, avoiding global locks.
-
Programmability: Any logic expressible in Leo can run privately – from DeFi protocols to on-chain games.
The trade-off is proving cost: generating SNARKs is heavier than signing a transaction.
Aleo mitigates this with delegated proving (outsourcing proof computation) and an open market of provers incentivized by block rewards.
How Aleo Compares
| System | Layer | Execution Model | Privacy Scope | Verification Cost | Notes |
|---|---|---|---|---|---|
| Ethereum | L1 | On-chain re-execution | Transparent | High | Every node re-runs all contracts |
| Zcash | L1 | Fixed SNARK circuit | Private payments only | Low | No general programmability |
| Aztec 2.0 | L2 (Ethereum) | Off-chain SNARKs, on-chain verify | Selective (L2 privacy) | Low | Limited contract logic, inherits Ethereum base layer |
| Mina | L1 | Recursive proofs of entire chain | Public | Low | Compresses state, not private |
| Secret Network | L1 | On-chain secure enclaves | Data-private | Medium | Relies on trusted hardware (SGX) |
| Aleo | L1 | Off-chain SNARK execution + on-chain verification | Fully private (inputs, outputs, identities) | Very low (verify-only) | First full-stack ZK-native L1 |
Aleo is the first blockchain where every application follows the same cryptographic workflow – no exceptions, no “private module” add-ons. Privacy isn’t a feature; it’s the default execution model.
In One Line
Aleo replaces “run everything everywhere” with “prove once, verify everywhere”, shifting blockchains from re-executors to verifiers.
Design Decisions and Trade-offs
Aleo’s design looks simple on the surface “compute locally, prove globally.”
But that simplicity hides a series of deliberate, deep architectural choices. Each one trades something familiar for something more powerful.
Why Aleo Chose Off-Chain Execution
Most blockchains demand that every node re-run every transaction.
It guarantees trust but limits throughput: everyone does the same work.
Aleo’s founders asked a radical question:
“What if we separate computation from verification?”
By moving execution off-chain, Aleo makes computation private and parallel:
-
Users (or provers) run programs locally using snarkVM.
-
The network only checks short proofs, not full computations.
-
Verification cost stays constant, no matter how complex the program was.
This separation gives Aleo the best of both worlds: scalability through off-chain work and trust through on-chain proofs.
It also changes the economics of computation. Instead of paying every validator to repeat the same code, you pay once, for the cryptographic proof that code was run correctly.
On a Normal Blockchain
When a transaction reaches the network, every node must re-run the same logic:
-
Execute the smart-contract or transaction code.
-
Recalculate all intermediate steps.
-
Update the global state.
-
Compare results with everyone else.
If 10 000 nodes exist, that same computation runs 10 000 times.
Every node sees the same data, does the same work, and stores the same result.
It’s secure but wasteful and, by design, completely public. Anyone watching can trace who did what and why.
On Aleo
When a transaction reaches the network, each node does something entirely different:
-
Takes the proof generated off-chain.
-
Verifies that the proof is valid for the program’s verification key.
-
Updates the Merkle-tree root to reflect the new commitments.
That’s it. Nodes never re-execute the program or see private inputs. They only check a compact mathematical receipt confirming that
“the computation was correct.”
Verification costs the same tiny amount of work, no matter how large the original computation was.
Every node still verifies (that’s what keeps it trustless),
but instead of re-running a program, they just check the math.
This single change, replacing re-execution with proof verification, turns blockchains from global computers into global verifiers.
Privacy as a Default, Not an Option
Other “private” systems bolt privacy on as a feature or middleware.
Aleo makes privacy the baseline. Every piece of state: balances, application data, even user identity, is stored as an encrypted record.
These records behave conceptually like UTXOs in Bitcoin:
They are individually owned, individually spent, and replaced with new ones during each transaction. The key difference is that Aleo’s records are fully encrypted. Only the owner (or someone with their view key) can decrypt or recognize them. To the network, records appear as opaque commitments.
If a developer wants something to be visible, they must explicitly mark it public in Leo.
This inversion of defaults forces a privacy-first mindset: everything is hidden unless you choose to expose it.
The upside is that every app on Aleo inherits strong privacy automatically.
The downside is that transparency tools, explorers, analytics dashboards, debuggers, can’t simply “read state” the way they do on transparent chains.
To inspect encrypted state, you must use a view key, or build tooling that respects encrypted records and their ownership.
It’s a small price to pay for turning “what you reveal” from an accident into a deliberate design choice.
Balancing Scalability and Decentralization
Aleo’s hybrid architecture combines Proof-of-Stake and Proof-of-Succinct-Work, but these layers involve different kinds of provers serving different roles.
-
Validators: staking ALEO. run AleoBFT, order transactions, verify zero-knowledge proofs, and finalize blocks. They secure consensus and maintain the encrypted global state.
-
Delegated Provers operate in the application flow. They generate zk-SNARK proofs for user transactions by taking an authorize request and producing the proof that validators will later verify. These provers directly support app usage and make private computation feasible on lightweight devices.
-
Puzzle Provers operate in the protocol’s incentive layer.
They compete to solve Aleo’s Proof-of-Succinct-Work (PoSW) coinbase puzzles, specialized SNARK challenges, to earn block rewards. This activity strengthens Aleo’s proving ecosystem, but it does not produce transaction proofs.
This split creates two proving markets:
- one powering user transactions,
- one powering network-level incentives and zk hardware advancement.
The trade-off is added complexity: Aleo must coordinate staked capital (validators), delegated proving (UX), and compute competition (PoSW). But the benefit is a self-reinforcing system:
As puzzle provers push zk hardware faster and cheaper, delegated provers become more efficient, improving UX, which attracts more users and more demand for proofs.
The result is an ecosystem where security, scalability, and private computation mutually reinforce each other.
The User Experience Trade-off
Privacy doesn’t come for free.
Generating a zk-SNARK proof can take a few seconds to a few minutes depending on hardware and circuit size. That’s manageable for high-value or infrequent operations, but too slow for lightweight clients like mobile wallets.
Aleo’s solution is delegated proving:
users can outsource the heavy computation to a third-party prover, while still retaining full control over their account.
Here’s how it works today:
-
Your wallet prepares an authorize request, signed with your private key.
This request contains the plaintext inputs and outputs of the program execution. It delegates the right to prove a specific transition, not to spend funds. -
You send this request to a delegated prover.
The prover can now see the inputs and outputs, delegation is not privacy-preserving. It simply shifts the computational burden. -
The prover generates the zk-SNARK proof using snarkVM and returns it to you.
-
You broadcast the proof to the network, where validators verify it using the public verification key.
The delegated prover cannot sign new transactions or alter the data, the proof would fail verification, but it does learn the contents of the request.
🚫 What the Prover Can and Can’t Do
| Action | Can the prover do it? | Why / How |
|---|---|---|
| Generate the proof | ✅ Yes | They receive an authorized request and the proving key. |
| Learn your private inputs or outputs | ⚠️ Yes | The authorize request is plaintext; delegated proving is not privacy-preserving. |
| Spend or move your funds | ❌ No | They lack your private key and cannot sign transactions. |
| Modify the transaction | ❌ No | Any change invalidates the proof. |
| Observe metadata (timing, proof size) | ✅ Yes | They see full transaction contents during proving. |
A privacy-preserving delegation system, where a prover could generate proofs without seeing private data, would require additional cryptographic techniques (e.g., witness encryption, FHE, or MPC-based proving).
This remains an active research area and is not yet part of Aleo’s proving pipeline.
Delegated proving today is about performance, not privacy.
It enables lightweight clients like mobile wallets and thin applications to participate in Aleo without requiring local proving hardware.
Over time, prover markets, independent services competing on latency, cost, and reliability, may become core infrastructure for Aleo’s UX.
Trust in Math vs Trust in Setup
Aleo’s security rests entirely on cryptography, but that math comes with a caveat.
Its zk-SNARK system (Groth16) requires a trusted setup: a one-time generation of public parameters. If all setup participants were malicious, they could, in theory, forge proofs.
To make that practically impossible, Aleo ran one of the largest multi-party ceremonies in blockchain history, over 2 200 contributors participated (Aleo Setup Ceremony Data; Aleo Technical Explanation). After that event, trust shifted entirely to mathematics:
as long as one participant was honest, no one can fake a proof (Aleo Community Road to Mainnet). The ceremony was audited, transparent, and publicly verifiable – a necessary trade-off for Aleo’s extreme efficiency.
Other proof systems like STARKs or Plonky2 remove trusted setups, but at much higher computational cost. Aleo’s choice of SNARKs reflects a bias toward performance and practicality, privacy that actually runs at scale.
What Aleo Gains – and What It Gives Up
| Design Choice | What It Enables | What It Costs |
|---|---|---|
| Off-chain execution | Massive scalability and privacy | More complex proving pipeline |
| zk-SNARK verification | Constant-time block validation | Requires trusted setup |
| Private-by-default state | True confidentiality | Harder tooling, limited analytics |
| Delegated proving | Mobile and lightweight UX | Introduces new trust surfaces |
| Hybrid PoS + PoSW | Balanced security and incentives | Two-layer economic complexity |
Aleo optimizes for privacy and verifiability first, not convenience. It gives up easy introspection in favor of cryptographic certainty. In doing so, it establishes a new design pattern for blockchains:
the chain as a verifier, not an executor.
Ecosystem and Go-To-Market
Aleo’s mainnet went live in September 2024, after more than three years of research, public testnets, and the largest zk-SNARK setup ceremony in blockchain history . It entered a market already full of Layer-1s and rollups, but its value proposition, a fully private, programmable base layer, immediately attracted developers building verifiable-yet-confidential applications .
Mainnet Launch and Community Traction
Aleo’s mainnet launch focused on both technical readiness and developer onboarding.
The network began with a deliberately small validator set, a maximum of 16 validators under Consensus Version 1, as defined in the protocol’s MAX_CERTIFICATES table.
As AleoBFT matured, the protocol increased this limit gradually across updates:
-
V1: 16 validators
-
V3: 25 validators
-
V5: 30 validators
-
V6: 35 validators
-
V9+ (current): 40 validators
These increases roll out only after rigorous performance and security testing, reflecting a cautious approach to decentralization and stability. The network today (Consensus Version 11) continues to cap the active validator set at 40.
Aleo’s testnets also attracted a large and active prover community.
Many of these operators have continued into mainnet as part of the Proof-of-Succinct-Work (PoSW) ecosystem, contributing compute power for network-level SNARK puzzles. PoSW remains permissionless, allowing any operator with suitable hardware to join and compete for rewards.
To accelerate ecosystem development, the Aleo Foundation allocated early grants and validator onboarding slots to builders rather than institutional custodians, reinforcing Aleo’s open-research ethos. Within the first quarter of mainnet, multiple of teams were already deploying or developing Leo programs across private DeFi, identity, compliance, and infrastructure tooling.
Developer Ecosystem
| Tool / Hub | Purpose | Notes / Sources |
|---|---|---|
| Leo Language + Toolchain | Write, test, and compile private programs | Leo app |
| Aleo SDK (JS / TS / Rust) | Wallets, web apps, and backend integrations | Aleo Developer Docs |
| Provable Explorer / API | Transaction viewer and developer interface | Aleo Explorer |
Aleo’s go-to-market strategy focuses on lowering the entry barrier for zero-knowledge developers through workshops, hackathons, and university collaborations (UC Berkeley, IC3, EPFL) .
Early Applications
Aleo’s early application ecosystem spans identity, payments, DeFi, infrastructure, and interoperability. Because privacy is native to the platform, many teams are exploring products that were not possible on transparent blockchains.
Identity and Reputation
- zPass – Aleo’s zero-knowledge identity verifier for KYC, age checks, and attestations. While the tool and site are not actively maintained today, it remains a canonical demonstration of private credential verification using Leo.
This early identity system shows how Aleo supports selective disclosure: users reveal only what is needed, not raw personal data.
DeFi and Payments
- AlphaSwap – a private AMM and liquidity routing system designed for encrypted order flow and hidden liquidity positions.
- Pondo Finance – liquid staking built natively on Aleo; staking positions remain private records instead of public balances.
More swap providers and private liquidity protocols are emerging, taking advantage of Aleo’s encrypted-state model.
Interop and Bridges
- Verulink Bridge – enables asset movement between Aleo and external chains, including Ethereum.
Several other interoperability projects are in development, expanding Aleo’s role as a private execution layer plugged into public ecosystems.
Tooling and Infrastructure
Aleo’s infrastructure layer is growing quickly, with a mix of open-source and commercial tools:
- Provable Explorer (official) – The canonical block explorer built by Provable, supporting encrypted-state representations and public function inspection.
- AleoScan – Community explorer supporting optional view-key based decryption for private records.
- Aleo Metrics (Artemis Analytics) – a data dashboard tracking Aleo network metrics, transaction sizes, block times, and prover activity.
- Aleo on Google Cloud Public Dataset – Aleo chain data accessible through Google Cloud’s BigQuery environment, enabling analytics over encrypted-state metadata.
- Prover Markets – emerging proof-as-a-service providers (e.g., zkCloud, Nebula Prover) building decentralized proving infrastructure .
These tools are crucial for making encrypted blockchains observable without compromising user privacy.
Industry Milestone
Aleo also became the first privacy Layer-1 listed on Coinbase, signaling strong institutional interest in privacy-preserving blockchain infrastructure.
Hardware Wallet Support and Key Security
Aleo’s multi-key account model – private, view, and compute keys – makes hardware integration more complex than in single-key ECDSA systems.
Still, secure hardware is strategically vital for three reasons:
-
Cold-storage of root keys: keep the private key offline while using derived keys (view / compute) for daily use.
-
View-key delegation: release a read-only key for scanning without spending authority.
-
Secure signing: hardware can authorize “authorize-request” messages used in delegated proving.
Current Status
-
Ledger Integration: as of early 2025, Ledger’s supported-assets list does not yet include Aleo (Ledger Supported Assets), and Leo Wallet confirms: “As of now, Leo Wallet does not support hardware wallets such as Ledger and Trezor.” (Leo Wallet FAQ)
-
Community Work: open-spec SDKs from Keystone / GridPlus enable Aleo derivation once official support lands.
-
Aleo SDK HID Bridge: introduces WebUSB / HID connectors so browser Leo apps can request hardware signatures without exposing raw keys .
5.5 Go-To-Market Focus
Aleo’s expansion strategy targets three fronts:
-
Developer First. Open SDKs + educational campaigns before retail onboarding .
-
Enterprise / Compliance. Partnerships with fintechs for privacy-preserving KYC and accounting .
-
Infrastructure / Hardware Acceleration. Encouraging GPU / FPGA proving services via PoSW rewards .
Aleo’s message remains consistent: privacy is a feature only if it’s usable.
By combining strong cryptography with practical tooling and hardware integration, Aleo aims to make zero-knowledge applications part of everyday development.
Risks, Debates, and Open Questions
Aleo’s architecture is bold. It merges advanced cryptography, new economic incentives, and a privacy-first design. But such innovation also introduces new risks – some technical, some economic, and some social.
This section outlines the key debates shaping Aleo’s next phase of maturity.
Proof Generation Latency & User Experience
Zero-knowledge proofs are fast to verify but expensive to generate. Even simple Leo programs can take seconds to prove on a laptop and longer on mobile devices. This creates a latency gap between building a transaction and broadcasting it.
Risk
Slow proving makes Aleo feel slow, regardless of how fast blocks are finalised, potentially limiting real-time use cases (gaming, streaming payments, synchronous interactions).
Mitigations & Emerging Solutions
-
Delegated Provers that offload computation from lightweight clients
-
Prover Markets where specialised operators offer low-latency proving services
-
Hardware acceleration (GPU → FPGA → ASIC)
-
Circuit-level and compiler-level optimisation in Leo and snarkVM
Open Question
Can Aleo deliver a mobile-first experience without centralising proving into a few industrial hardware operators?
Delegated Proving: Trust & Privacy Boundaries
Delegated proving dramatically improves UX, but today, it is not privacy-preserving.
Authorize requests contain plaintext inputs and outputs, meaning a delegated prover learns the full contents of the transaction they are proving.
Risk
Users may mistakenly assume delegated proving hides private data.
In reality, delegated provers see everything except the spending key.
Mitigation
Strict boundaries: delegated provers cannot sign transactions or modify the computation (the proof would fail), and can only prove transitions explicitly authorised by the user.
Open Research Direction
Privacy-preserving delegated proving, using MPC, witness encryption or obfuscation, is an exciting frontier but not yet practical.
This challenge is central to Aleo's long-term UX strategy:
how to combine performance with private proving, especially at scale.
Interoperability & Cross-Chain Verification (ARC-100)
As Aleo integrates with other ecosystems, especially EVM and IBC chains, the main risks shift from computation to state correctness.
ARC-100 formalises best practices for:
-
cross-chain message formats
-
proof verification rules
-
timestamp and freshness guarantees
-
replay-attack protection
-
trust boundaries between encrypted and transparent chains
-
how private state should be referenced externally without leaking information
Risks if done incorrectly
-
replayed proofs on external chains
-
mis-interpreted encrypted state
-
“half-verified” cross-chain messages
-
bridge operators relying on unsafe assumptions
Mitigation
ARC-100’s cross-chain canonical structure ensures that Aleo’s encrypted commitments and proofs remain unambiguous on any external chain.
Open Question
How do external chains verify Aleo proofs without trusting Aleo consensus?
And conversely, how does Aleo consume external state safely without breaking privacy?
This is one of the most important long-term challenges for Aleo.
Private State & View-Key Governance
Aleo’s encrypted state introduces entirely new governance and UX questions:
-
Should applications require users to share view keys for audits or regulated contexts?
-
Should view keys be revocable or scoped?
-
How should private-state disclosure be managed across enterprise, compliance, or legal workflows?
-
How can users selectively reveal specific fields inside encrypted records without exposing everything?
Risk
Poorly designed disclosure policies can recreate central points of trust or leak private information unintentionally.
Mitigation
Aleo’s selective-disclosure model gives developers fine-grained control over which data is public, private, or conditionally revealed.
Open Question
What are the best practices for privacy-preserving compliance, and how should they be enforced at the application layer?
Ecosystem Maturity & Tooling
Aleo’s developer ecosystem is expanding rapidly, but private-by-default systems introduce challenges that transparent chains never had to solve.
Tools like indexers, debuggers, or analytics engines cannot simply read plaintext state — they must interpret encrypted records, respect view-key boundaries, and work with commitments instead of account balances.
Risk
The absence of mature privacy-aware tooling (encrypted indexers, circuit debuggers, record scanners, and cross-chain verifiers) can slow application development and make onboarding more difficult for teams used to public-state blockchains like Ethereum or Cosmos.
Mitigation
Aleo’s SDKs, Leo Playground, and new explorers, including Provable Explorer and community tools like AleoScan, are helping close this gap.
Additionally, emerging standards such as ARC-100 define how encrypted state, proofs, and cross-chain messages should be structured, providing a foundation for interoperable tooling across the ecosystem.
Open question
Can privacy-first systems achieve the same level of developer ergonomics as transparent chains, or will Aleo require a new generation of privacy-aware infrastructure to match that experience while preserving confidentiality?
Final Thoughts / TL;DR
Aleo represents a quiet but radical shift in how blockchains work.
Instead of asking every node to redo the same computation, it asks every user to prove theirs – privately, locally, and cryptographically.
The result is a system where trust no longer comes from transparency, but from mathematics.
By combining zero-knowledge proofs, off-chain execution, and an on-chain verification layer, Aleo turns the blockchain from a global computer into a global verifier.
Computation moves to the edge; privacy becomes the default; and consensus becomes a fast, lightweight proof check.
It’s not without trade-offs – proving time, hardware concentration, and regulatory uncertainty all remain open questions. But Aleo’s experiment shows that the tools for private, verifiable computation are no longer theoretical.
They’re real, deployable, and beginning to scale.
If Bitcoin proved that code can enforce money, and Ethereum proved that code can enforce logic, Aleo is proving that code can enforce privacy – without asking anyone to trust what they can’t see.



